- cross-posted to:
- [email protected]
- cross-posted to:
- [email protected]
Amidst the glossy marketing for VPN services, it can be tempting to believe that the moment you flick on the VPN connection you can browse the internet with full privacy. Unfortunately this is quite far from the truth, as interacting with internet services like websites leaves a significant fingerprint. In a study by [RTINGS.com] this browser fingerprinting was investigated in detail, showing just how easy it is to uniquely identify a visitor across the 83 laptops used in the study.
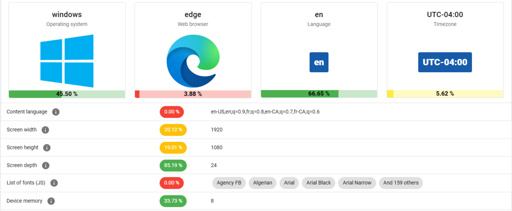
As summarized in the related video (also embedded below), the start of the study involved the Am I Unique? website which provides you with an overview of your browser fingerprint. With over 4.5 million fingerprints in their database as of writing, even using Edge on Windows 10 marks you as unique, which is telling.


Does anonymous mode browsing+VPN improve this? I would think it would
Part of the reason Tor is good is because it generates the same fingerprint for all users (part of the reason you shouldn’t install additional extensions on it, by the way). Mullvad browser tries to do this but without the Tor network.
How would tor do that? As far as I understand the fingerprint is an aggregate of multiple very specific variables ie https://amiunique.org/fingerprint. Sure tor might set some (or a lot) to a default but some are very difficult to circumvent such as the rendering of specific shapes and text.
You can’t hide or get rid of the browser fingerprint, but some addons can help to randomize it so it looks like you’re using a different device every time you visit a site.
Personally, I don’t care if a site can fingerprint me. As long as they can’t tie that fingerprint to a rich data set.
So I make sure that each domain gets a different fingerprint response. That means that a site can validate that I’m still the same user, but any XSS attempting fingerprint based data exchange just gets garbage.
And how do you go about that? Do you adjust your window size and extensions on a site-by-site basis?
Is Firefox’s claimed Anti fingerprinting technology any good?
Some, but only if you’re using a very common device (i.e. Dell Latitude) with Windows. Browser fingerprinting gives up hardware specs, so hiding by blending in only works when your hardware is hard to pin down.
Use a browser that hides hardware specs, like Mullvad or Libreworlf. Even Brave is ok.